Cybersecurity for Business
Protect your critical digital assets from cyberattacks.
In an increasingly connected world, cybersecurity is no longer optional. Every digital interaction—whether through email, devices, or networks—presents potential vulnerabilities. At Copeland Technology Solutions, we take a proactive, layered approach to ensure your business stays secure, resilient, and ready for the future.
Our account managers and staff provide education to your team via social media, training and reoccurring security reviews.
Learn about Cybersecurity
Cybersecurity Overview

Cybersecurity isn’t just targeting large corporations—they can impact businesses of all sizes and individuals alike. With threats evolving daily, staying ahead requires a comprehensive strategy and expert tools. That’s where we come in.
As a whole, we are aggregating a tremendous amount of data compared to ten or even five years ago. It is no longer just customer and vendor data we are storing but employee data, personal data of customers, credit card data and more. With more data comes more responsibility to protect that data.
Beyond developing plans for our clients, implementing the strategies and proactively monitoring their digital security, it’s our role as a managed services provider to educate technology-reliant businesses on cybersecurity best practices.
Please take a moment to check your company’s cybersecurity preparedness.
This 3-minute checklist will help you better understand the strengths and weaknesses of your cybersecurity program.


Your First Line of Defense: Patch Management
Outdated systems create gaps in your defenses, leaving your business vulnerable to cyberattacks and operational downtime. Inconsistent patching can lead to security breaches, lost productivity, and expensive recoveries.
Our proactive Patch Management keeps your systems up-to-date with the latest security patches, reducing vulnerabilities and minimizing downtime. Preventing disruptions before they occur helps keep operations running smoothly and the team productive.
Managed Detection and Response
Cyber threats evolve daily, and a single undetected attack can result in data breaches, operational paralysis, and financial losses. Most businesses lack the resources to monitor and respond to these threats effectively.
Our Managed Detection and Response solution uses industry-leading technology to detect, isolate, and stop threats before they disrupt your network. By reducing the risk of costly breaches, we protect your bottom line and allow your team to stay focused on growth.
SIEM Log Aggregation
When your network activity is scattered across systems, it’s easy for threats to slip through the cracks. Without centralized visibility, you’re left vulnerable to attacks that can damage your reputation and bottom line.
Our Security Information and Event Management (SIEM) service monitors your network in real time, providing clear, actionable insights to proactively address threats. This protection safeguards your reputation and minimizes the financial impact of potential incidents.
Email Protection and Monitoring
Phishing, malware, and spam make email one of the most common entry points for cyberattacks. A single malicious email can compromise sensitive data, disrupt operations, and incur significant recovery costs.
Our AI-powered Email Protection solution filters and blocks threats before they reach your inbox. By keeping your team and data secure, we help you avoid costly downtime and protect your business from avoidable disruptions.
Extra Layer of Protection: Vulnerability Scanning
Unchecked vulnerabilities in your network can lead to devastating security breaches, eroding trust and harming your brand. Unidentified weaknesses puts your business at risk of significant financial and reputational damage.
Our continuous Vulnerability Scanning identifies and addresses potential weaknesses across your network so they can be patched and mitigated. By strengthening your defenses proactively, we help you avoid setbacks and maintain confidence in your security.
At Copeland Technology Solutions, we don’t just address cybersecurity issues—we provide proactive solutions that minimize risks and reduce the likelihood of costly incidents. With our cybersecurity tools, you can focus on running and growing your business with confidence. Let us help you move your business forward!
Building a Stronger Defense: Practical Steps to Protect Your Data
While you can never completely protect your data 100%, you can make it more difficult for an attacker to get in or get what they want by doing some of these things.
Patching Software
When attackers exploit Windows or Internet Explorer or any other application, security patches are released to plug the hole. Microsoft is being more aggressive with this in new versions of Windows but you have to pay attention to all software as it is just not Microsoft anymore. Adobe, Chrome, Firefox and other applications need to be updated to plug the holes.
What You Can Do: Microsoft Service Providers and internal IT departments are utilizing RMM (Remote Monitoring and Management) applications that take care of patch management and can notify you if software is out of date. These are typically per-device -per-month services that add large amounts of value.
Public Drives
Most companies have public drives that allow the organization to share data. Many of these are open to all users who authenticate. If there is any data that is confidential on these drives, hackers will go to this first as it is “low-hanging fruit.”
What You Can Do: Begin limiting the use of public drives to non-confidential information. If you need to share confidential information, utilize a Document Management System or lock down the folders with tight permissions for specific users.
Protect Mobile Devices and Laptops
As more employees work remotely or on the go, the risks to mobile devices and laptops have grown. These devices often contain sensitive company data, making them prime targets for theft or unauthorized access.
What You Can Do: First off, encrypt any device that has the ability to be encrypted. This will require a thief to know the password of the machine to get the data. For all devices, utilize a mobile device management tool (Microsoft uses Intune) to control and wipe these devices if necessary. You can also ensure users are trained on secure practices for mobile device use.
Remote Access
Remote work has become the norm, but allowing external devices to connect to your network introduces additional risks, especially if those devices lack proper security measures. Most home PCs do not have proper anti-virus protection and the amount of Internet traffic is usually higher resulting in greater risk.
What You Can Do: Require secure VPN tunnels for all remote connections, rather than opening Remote Desktop Protocol (RDP) access through your router.
Implement policies mandating that all remote devices:
· Use up-to-date antivirus software.
· Receive regular patches and updates.
· Have strong, complex passwords.
Whenever possible, provide company-managed devices for remote work to maintain full control over security measures.
Secure Shared Data with Modern Cloud Solutions
Shared drives were once the go-to solution for collaboration, but they often expose sensitive data to unnecessary risks. Modern cloud storage solutions like Microsoft SharePoint or OneDrive for Business provide secure, scalable, and easily managed alternatives.
What You Can Do: Use SharePoint to securely store, share, and collaborate on files. With its built-in permission settings and version history, you can control who accesses your data and ensure changes are tracked.
Enable conditional access policies to restrict data access based on user location, device type, or security compliance.
Audit file access regularly to identify unusual or unauthorized activity.
Multi-Factor Authentication (MFA)
Passwords alone are no longer enough to secure sensitive accounts and systems. Multi-Factor Authentication (MFA) adds a critical layer of protection by requiring users to verify their identity through multiple methods—such as a password and a code sent to their mobile device.
What You Can Do: Enable MFA Everywhere. Protect critical systems like email, VPNs, cloud storage, and financial accounts with MFA. Encourage employees to use authentication apps like Microsoft Authenticator for a more secure experience than SMS codes. Make MFA mandatory for all users, especially those with access to administrative or sensitive data.
The Biggest Threat: Email Phishing
Your Inbox Is the Front Line of Cybersecurity
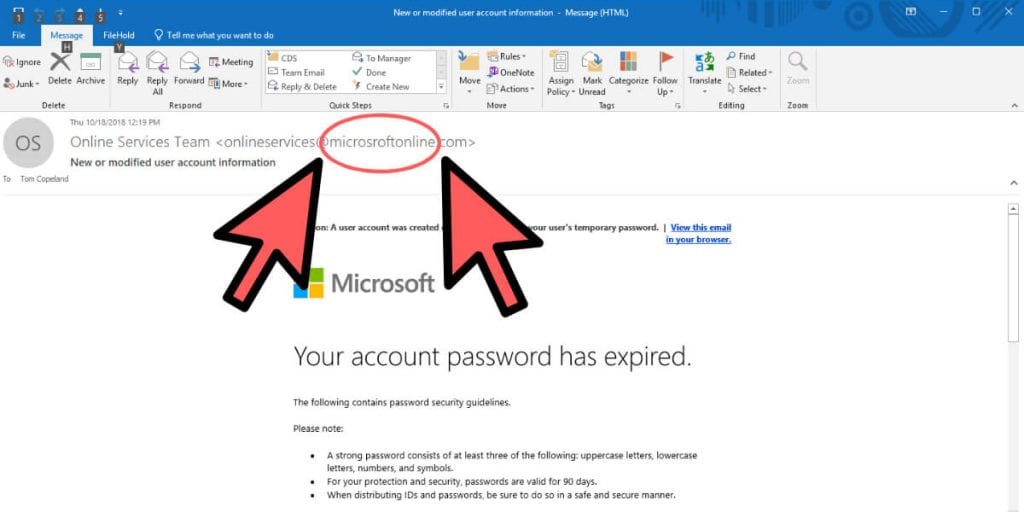
Email phishing is one of the most common and effective ways cybercriminals gain access to sensitive information. These emails are designed to look legitimate—sometimes even urgent—luring unsuspecting individuals into providing passwords, financial data, or other confidential information.
This is just Microsoft asking for some sensitive information so they can help your account – right? Look again, and you’ll see that it is in fact NOT from Microsoft at all and you’ll find subtle red flags: a suspicious email address, unusual phrasing, or an unexpected request.
Phishing emails are not just a nuisance—they can cripple organizations. Once a single employee clicks a malicious link or downloads an infected attachment, your entire network could be at risk. In today’s connected world, a lack of awareness can lead to data breaches, financial loss, and reputational damage.
See the information below for important information that your employees need to protect your company from email phishing attacks.
Here are some of the common warning signs to look for:
- Poor spelling and grammar
- Incorrect use of common phrases
- Be wary of the sender needing an “urgent” response
- Hover over the sender name to reveal the sender email address
- Be cautious of long strings of incoherent letters and number
Protect yourself from phishing scams by doing the following:
- If you are suspicious of the email, NEVER click on links or attachments within the email
- If the suspicious email comes from a place where you have an account, like Netflix, go directly to your online account via an internet browser rather than going through the email
- Never share personal information or credentials through an email you receive. Always go directly to the source to ensure you are interacting with the REAL organization
- If you are suspicious of the email, do NOT forward it to a third party for verification, as this could lead to someone else clicking on a virus. Simply delete the email


How Hackers Try to Find Your Business
Business infrastructure is evolving rapidly, and cybercriminals are constantly finding new ways to exploit vulnerabilities. While high-profile data breaches in industries like finance, retail, energy, social media, and telecommunications dominate the headlines, small to medium-sized businesses (SMBs) are increasingly at risk.
How Hackers Find You
Hackers often use automated tools, known as bots, to scan the internet for devices with vulnerabilities. These bots systematically look for weaknesses—outdated software, open ports, or misconfigured systems. Hackers don’t discriminate based on location, industry, or company size. If there’s a vulnerability, they’ll exploit it.
Once inside, they carefully explore your network to determine what they can access. Their primary goals are to:
· Elevate Permissions: Gain higher-level access to install malicious software or extract sensitive data.
· Steal Data: Gather valuable information, including passwords, financial data, and proprietary business details.
· Cause Damage: Encrypt data for ransomware attacks, open network backdoors, or disrupt operations.
Shockingly, a typical hacker can remain undetected in a network for an average of 6 months, quietly collecting information and preparing for a full-scale attack.
It is imperative that your management team has a Business Continuity Plan that outlines how you will continue to operate during and after a disruptive event. We can no longer think of a breach as “if it happens” but “when it happens.”

Cybersecurity Resources

Protect Your Business. Protect Your Community.
Cyberattacks continue to rise because they work. Why? Many organizations fail to make the necessary investments in time, money, and resources to protect against them. Even worse, most attacks aren’t highly sophisticated—they exploit the simplest vulnerabilities that could easily be addressed with proper preparation.
At Copeland Technology Solutions, we understand the critical importance of safeguarding your business. It’s not just about avoiding downtime—it’s about protecting your employees, your customers, and the local community that relies on you.
Cybersecurity Services with Copeland
Managed IT Services

We work on cybersecurity services all day, every day. If you have any questions about your plans or the health of your technology systems, get in touch with us and let’s talk technology.

